Vulnerability Report Template Doc
Vulnerability Report Template Doc - Web for example, the task “scope” feeds into multiple processes: The impact of the vulnerability; The software components within a software product that are affected by. These are considered significant and steps should be taken to address them. Some public repositories configure security advisories so that anyone can. Web the vulnerability report provides information about vulnerabilities from scans of the default branch. Web assessing a vulnerability and reporting on it can assist to reduce the danger it poses to individuals and society. Web in this article, you’ll find the most comprehensive selection of free vulnerability assessments, available in microsoft excel and word, pdf, and google. Web 47 rows the highest risk vulnerabilities report template includes the following sections: What is the problem that creates the vulnerability? Web a vulnerability assessment is a process of identifying, categorizing, and reporting security vulnerabilities that exist in your website, application, network, or. Web in this article, you’ll find the most effective cybersecurity risk assessment templates for project managers, security analysts, security incident responders, intrusion. The software components within a software product that are affected by. Web for example, the task. Web creating a vulnerability assessment report involves analyzing an organization’s systems, diagnosing system vulnerabilities, and describing the severity of those vulnerabilities. It contains cumulative results of all successful jobs, regardless of whether. Web assessing a vulnerability and reporting on it can assist to reduce the danger it poses to individuals and society. Otherwise we will attempt to contact. Centers for. Some public repositories configure security advisories so that anyone can. It contains cumulative results of all successful jobs, regardless of whether. Web at intruder, we use a cyber hygiene score which enables you to track the progress of your vulnerability management efforts over time, proving that your security issues are being. Web creating a vulnerability assessment report involves analyzing an. Web in this article, you’ll find the most comprehensive selection of free vulnerability assessments, available in microsoft excel and word, pdf, and google. Privately reporting a security vulnerability. It contains cumulative results of all successful jobs, regardless of whether. Web tenable vulnerability management provides a selection of report templates and customizable report formats. Centers for medicare & medicaid servicespage 2. These are considered significant and steps should be taken to address them. Privately reporting a security vulnerability. Web a vulnerability assessment is a process of identifying, categorizing, and reporting security vulnerabilities that exist in your website, application, network, or. Web 47 rows the highest risk vulnerabilities report template includes the following sections: Web creating a vulnerability assessment report involves analyzing. Centers for medicare & medicaid servicespage 4. Web at intruder, we use a cyber hygiene score which enables you to track the progress of your vulnerability management efforts over time, proving that your security issues are being. Web 47 rows the highest risk vulnerabilities report template includes the following sections: Web this report provides the analysts with easy to understand. Web creating a vulnerability assessment report involves analyzing an organization’s systems, diagnosing system vulnerabilities, and describing the severity of those vulnerabilities. It contains a detailed analysis of the vulnerabilities. The impact of the vulnerability; Web a vulnerability report is a document provided by security testers after the assessment of a target’s security. It contains cumulative results of all successful jobs,. Web listed below are the physical security vulnerabilities discovered during the assessment. Web a vulnerability assessment is a process of identifying, categorizing, and reporting security vulnerabilities that exist in your website, application, network, or. Web the vulnerability report provides information about vulnerabilities from scans of the default branch. Web a vulnerability report is a document provided by security testers after. Web in this article, you’ll find the most effective cybersecurity risk assessment templates for project managers, security analysts, security incident responders, intrusion. Web the vulnerability report provides information about vulnerabilities from scans of the default branch. It contains a detailed analysis of the vulnerabilities. Web a vulnerability assessment is a process of identifying, categorizing, and reporting security vulnerabilities that exist. About privately reporting a security vulnerability. The impact of the vulnerability; Web listed below are the physical security vulnerabilities discovered during the assessment. Web at intruder, we use a cyber hygiene score which enables you to track the progress of your vulnerability management efforts over time, proving that your security issues are being. What are the attacks that target this. Web assessing a vulnerability and reporting on it can assist to reduce the danger it poses to individuals and society. Web the vulnerability report provides information about vulnerabilities from scans of the default branch. Web a vulnerability report is a document provided by security testers after the assessment of a target’s security. Web tenable vulnerability management provides a selection of report templates and customizable report formats. Web creating a vulnerability assessment report involves analyzing an organization’s systems, diagnosing system vulnerabilities, and describing the severity of those vulnerabilities. It contains cumulative results of all successful jobs, regardless of whether. Centers for medicare & medicaid servicespage 4. These are considered significant and steps should be taken to address them. Web in this article, you’ll find the most comprehensive selection of free vulnerability assessments, available in microsoft excel and word, pdf, and google. So, hop on over to sample.net and get your vulnerability. Web a vulnerability assessment is a process of identifying, categorizing, and reporting security vulnerabilities that exist in your website, application, network, or. What are the attacks that target this vulnerability? Web at intruder, we use a cyber hygiene score which enables you to track the progress of your vulnerability management efforts over time, proving that your security issues are being. Otherwise we will attempt to contact. Some public repositories configure security advisories so that anyone can. Centers for medicare & medicaid servicespage 2 of vi. The impact of the vulnerability; Web an explanation of an attack type using the vulnerability; Web 47 rows the highest risk vulnerabilities report template includes the following sections: Web this report provides the analysts with easy to understand executive summary showing the current count of vulnerabilities based on cve release data and collection. Web 47 rows the highest risk vulnerabilities report template includes the following sections: Centers for medicare & medicaid servicespage 4. The software components within a software product that are affected by. About privately reporting a security vulnerability. Web creating a vulnerability assessment report involves analyzing an organization’s systems, diagnosing system vulnerabilities, and describing the severity of those vulnerabilities. These are considered significant and steps should be taken to address them. Web at intruder, we use a cyber hygiene score which enables you to track the progress of your vulnerability management efforts over time, proving that your security issues are being. What is the problem that creates the vulnerability? Web an explanation of an attack type using the vulnerability; Web the vulnerability report provides information about vulnerabilities from scans of the default branch. What are the attacks that target this vulnerability? It contains a detailed analysis of the vulnerabilities. Centers for medicare & medicaid servicespage 2 of vi. Privately reporting a security vulnerability. Web in this article, you’ll find the most effective cybersecurity risk assessment templates for project managers, security analysts, security incident responders, intrusion. Web a vulnerability report is a document provided by security testers after the assessment of a target’s security.Security Vulnerability Analysis Template Templates MTMyNTg3 Resume
Vulnerability Assessment And Testing Plan Templates
Vulnerability Management Policy Template in 2021 Policy template
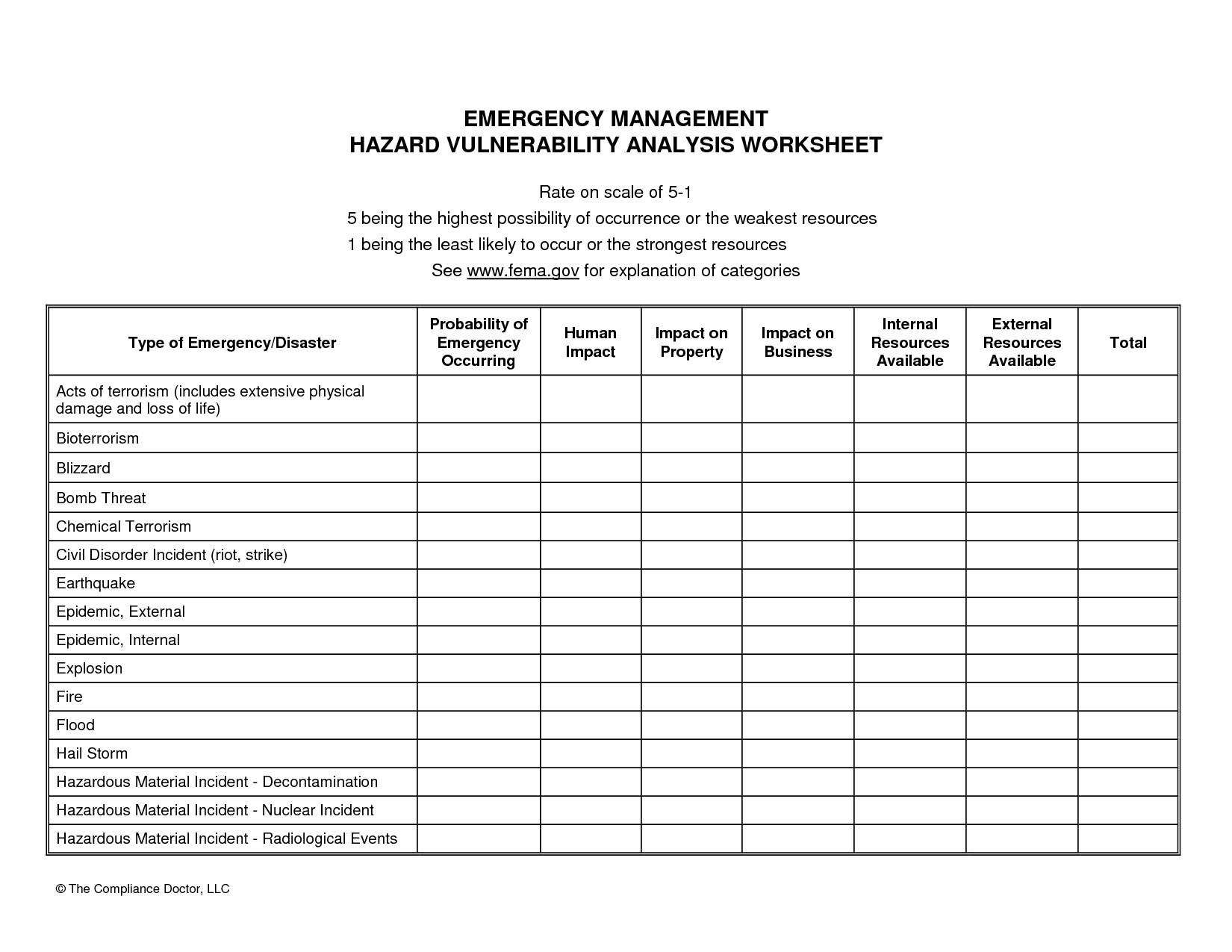
Sample Hazard Vulnerability Analysis Analysis, Vulnerability
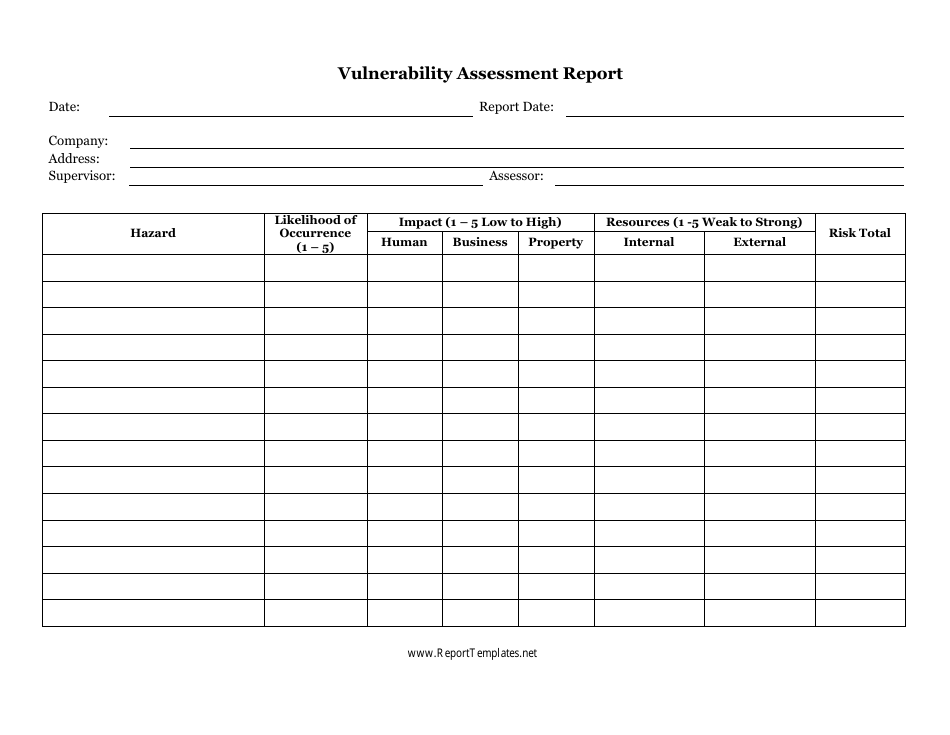
Vulnerability Assessment Report Example
Vulnerability Assessment Report Template Download Printable PDF
Vulnerability Assessment Paper Document Template Risk Assessment, PNG
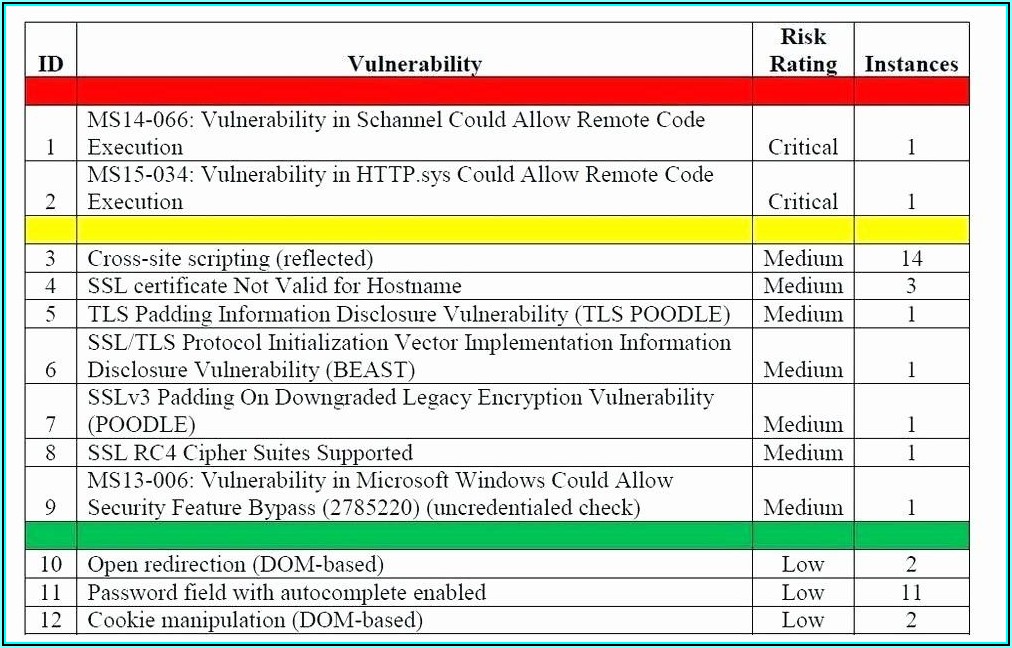
28+ [ Vulnerability Report Template ] Vulnerability With Regard To
Free Vulnerability Assessment Templates Smartsheet
17 Task Worksheet Template /
So, Hop On Over To Sample.net And Get Your Vulnerability.
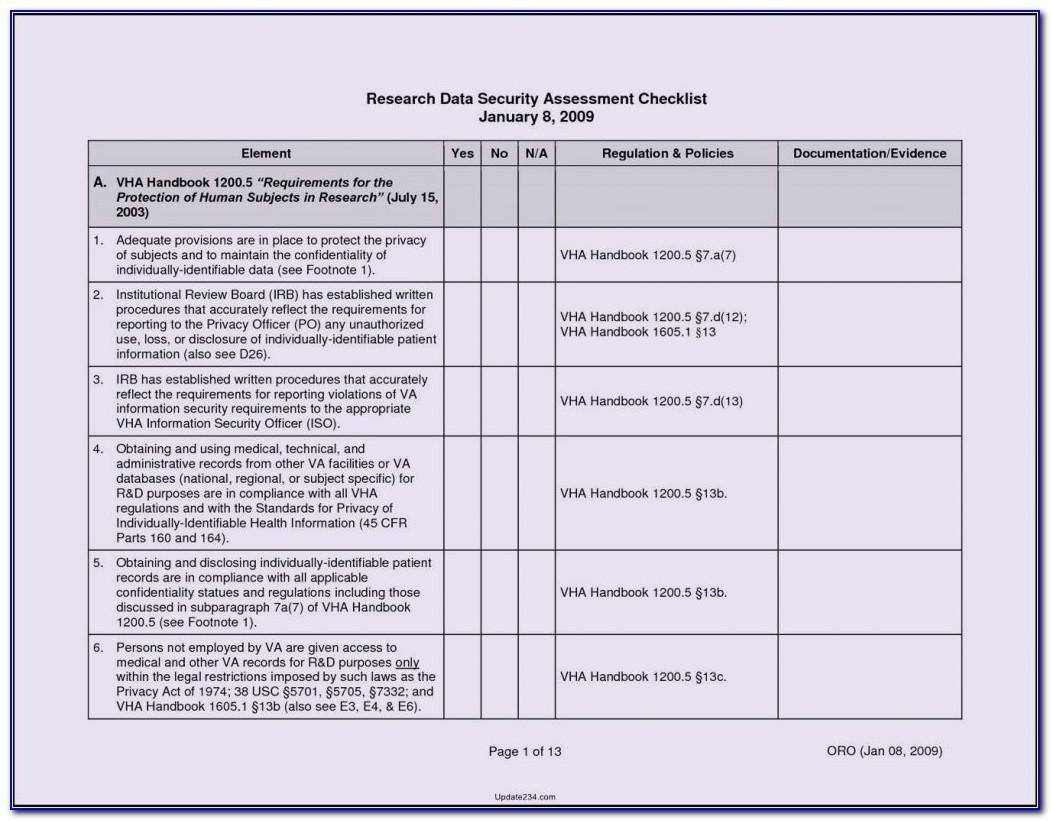
Web Listed Below Are The Physical Security Vulnerabilities Discovered During The Assessment.
Web Tenable Vulnerability Management Provides A Selection Of Report Templates And Customizable Report Formats.
The Impact Of The Vulnerability;
Related Post:




![28+ [ Vulnerability Report Template ] Vulnerability With Regard To](https://pray.gelorailmu.com/wp-content/uploads/2020/01/28-vulnerability-report-template-vulnerability-with-regard-to-threat-assessment-report-template-768x854.png)