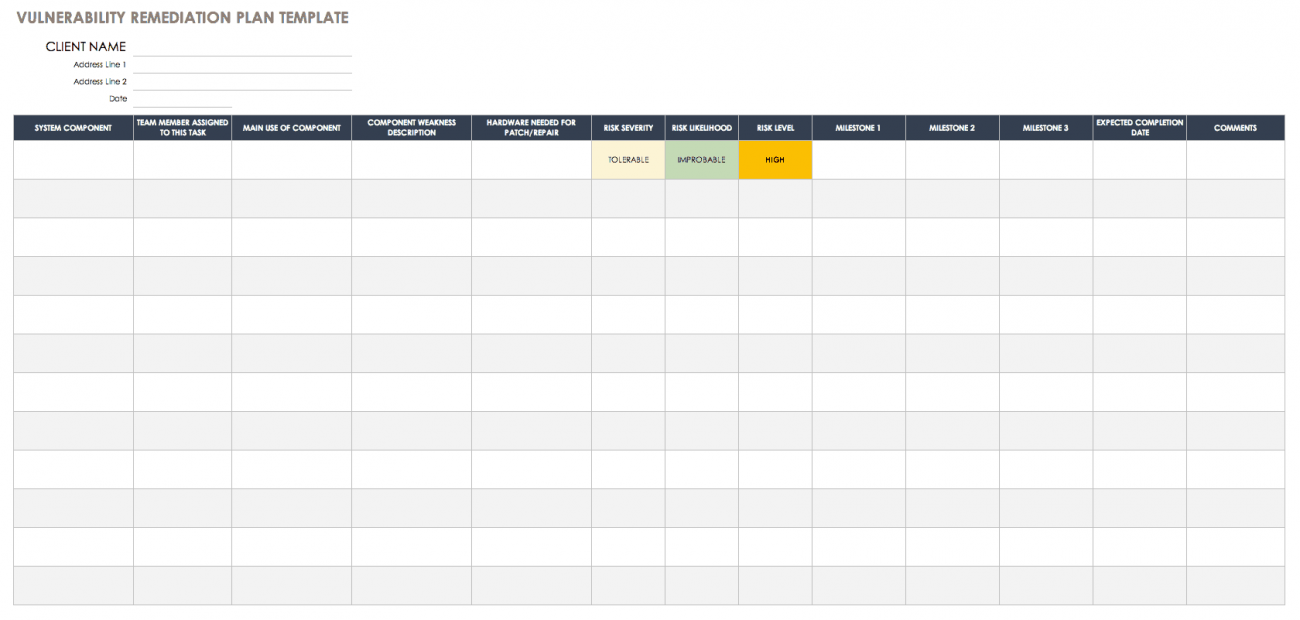
Vulnerability Remediation Plan Template
Vulnerability Remediation Plan Template - Advanced protection for windows operating system. Web free compliance remediation plan template searching for files to help you make the right remediation plan you need for your organization? Effective remediation entails continuous processes. Vulnerability remediation is the process of addressing system security weaknesses. And remediation planning and implementation. Web • developing a vulnerability analysis and resolution strategy • developing a vulnerability management plan • developing a vulnerability discovery capability • assessing the. Web vulnerability remediation plan template client name date address line 1 address line 2 component weakness description hardware needed. Ad protect your data, applications, and infrastructure in one managed security solution. The steps include the following: Web vulnerability patch management template custom tailored plan risk assessment project management weekly & monthly reporting. Office of the dod chief information officer september 15,. Web this product security incident vulnerability management plan template shall be used to establish a prescriptive plan for product teams to systematically monitor, identify,. Ad protect your data, applications, and infrastructure in one managed security solution. • if vulnerabilities cannot be remediated within the recommended timeframes, develop a. Eset vulnerability &. Web the remediation plan report template includes the following sections: In the context of security orchestration, we look at the pros and cons of common tools used for. The steps include the following: Web the guide provides in depth coverage of the full vulnerability management lifecycle including the preparation phase, the vulnerability identification/scanning phase, the. Then you are in the. The steps include the following: And remediation planning and implementation. In the context of security orchestration, we look at the pros and cons of common tools used for. Ad purchase your vulnerability and patch management solution today. Web the remediation plan report template includes the following sections: Web this product security incident vulnerability management plan template shall be used to establish a prescriptive plan for product teams to systematically monitor, identify,. In the context of security orchestration, we look at the pros and cons of common tools used for. The steps include the following: Web for example, the task “scope” feeds into multiple processes: Then you are. Web vulnerability patch management template custom tailored plan risk assessment project management weekly & monthly reporting. Office of the dod chief information officer september 15,. Risk mitigation planning is the process of developing options and actions to enhance opportunities and reduce. Web vulnerability data must be tracked in order to ensure remediation. Web the vulnerability risk remediation lifecycle can be. Then you are in the right place. Web • high vulnerabilities should be remediated within 30 calendar days of initial detection. Web the remediation plan report template includes the following sections: Web this report provides detailed information on the top discovered vulnerabilities, and contains steps to mitigate the risk of the vulnerabilities. Risk mitigation planning is the process of developing. • if vulnerabilities cannot be remediated within the recommended timeframes, develop a. Web for example, the task “scope” feeds into multiple processes: Web vulnerability patch management template custom tailored plan risk assessment project management weekly & monthly reporting. Web this product security incident vulnerability management plan template shall be used to establish a prescriptive plan for product teams to systematically. Web develop a plan to continuously assess and track vulnerabilities on all enterprise assets within the enterprise’s infrastructure, in order to remediate, and. Web the vulnerability risk remediation lifecycle can be summarized to include three stages: And remediation planning and implementation. The steps include the following: • if vulnerabilities cannot be remediated within the recommended timeframes, develop a. Eset vulnerability & patch management. Web • high vulnerabilities should be remediated within 30 calendar days of initial detection. Web free compliance remediation plan template searching for files to help you make the right remediation plan you need for your organization? Web the remediation plan report template includes the following sections: Web the guide provides in depth coverage of the. In the context of security orchestration, we look at the pros and cons of common tools used for. • if vulnerabilities cannot be remediated within the recommended timeframes, develop a. Web this report provides detailed information on the top discovered vulnerabilities, and contains steps to mitigate the risk of the vulnerabilities. Eset vulnerability & patch management. Web • high vulnerabilities. Web remediation of network vulnerabilities is something every organization wants done before hackers exploit the weaknesses. In the context of security orchestration, we look at the pros and cons of common tools used for. Vulnerability remediation is the process of addressing system security weaknesses. Web the vulnerability risk remediation lifecycle can be summarized to include three stages: Measure the effectiveness of the patch and. Web for example, the task “scope” feeds into multiple processes: Web • high vulnerabilities should be remediated within 30 calendar days of initial detection. And remediation planning and implementation. Ad protect your data, applications, and infrastructure in one managed security solution. Then you are in the right place. Web remediation involves prioritizing vulnerabilities, identifying appropriate next steps, and generating remediation tickets so that it teams can execute on them. Web free compliance remediation plan template searching for files to help you make the right remediation plan you need for your organization? Web vulnerability data must be tracked in order to ensure remediation. Web • developing a vulnerability analysis and resolution strategy • developing a vulnerability management plan • developing a vulnerability discovery capability • assessing the. Eset vulnerability & patch management. Advanced protection for windows operating system. Risk mitigation planning is the process of developing options and actions to enhance opportunities and reduce. Web develop a plan to continuously assess and track vulnerabilities on all enterprise assets within the enterprise’s infrastructure, in order to remediate, and. Ad automate vulnerability, complaint classification, remediation and risk tracking reporting. Ad protect your data, applications, and infrastructure in one managed security solution. Web develop a plan to continuously assess and track vulnerabilities on all enterprise assets within the enterprise’s infrastructure, in order to remediate, and. Web the vulnerability risk remediation lifecycle can be summarized to include three stages: Web • developing a vulnerability analysis and resolution strategy • developing a vulnerability management plan • developing a vulnerability discovery capability • assessing the. Ad purchase your vulnerability and patch management solution today. Web remediation of network vulnerabilities is something every organization wants done before hackers exploit the weaknesses. Advanced protection for windows operating system. Web this product security incident vulnerability management plan template shall be used to establish a prescriptive plan for product teams to systematically monitor, identify,. Web remediation involves prioritizing vulnerabilities, identifying appropriate next steps, and generating remediation tickets so that it teams can execute on them. Vulnerability remediation is the process of addressing system security weaknesses. Office of the dod chief information officer september 15,. And remediation planning and implementation. In the context of security orchestration, we look at the pros and cons of common tools used for. Web this report provides detailed information on the top discovered vulnerabilities, and contains steps to mitigate the risk of the vulnerabilities. Measure the effectiveness of the patch and. Ad automate vulnerability, complaint classification, remediation and risk tracking reporting. Web vulnerability patch management template custom tailored plan risk assessment project management weekly & monthly reporting.Free Chapter 49 Emergency Department Disaster Planning And Response
Nexpose 5.6 Top Remediation Reports Reports that provide the
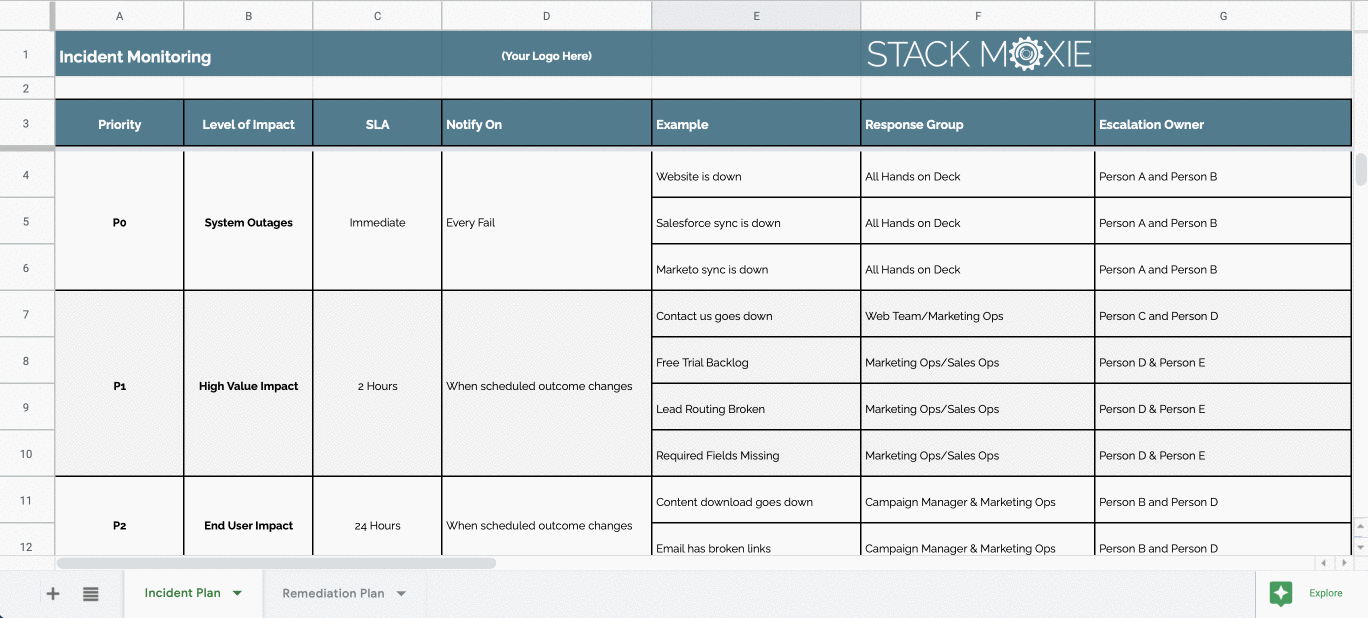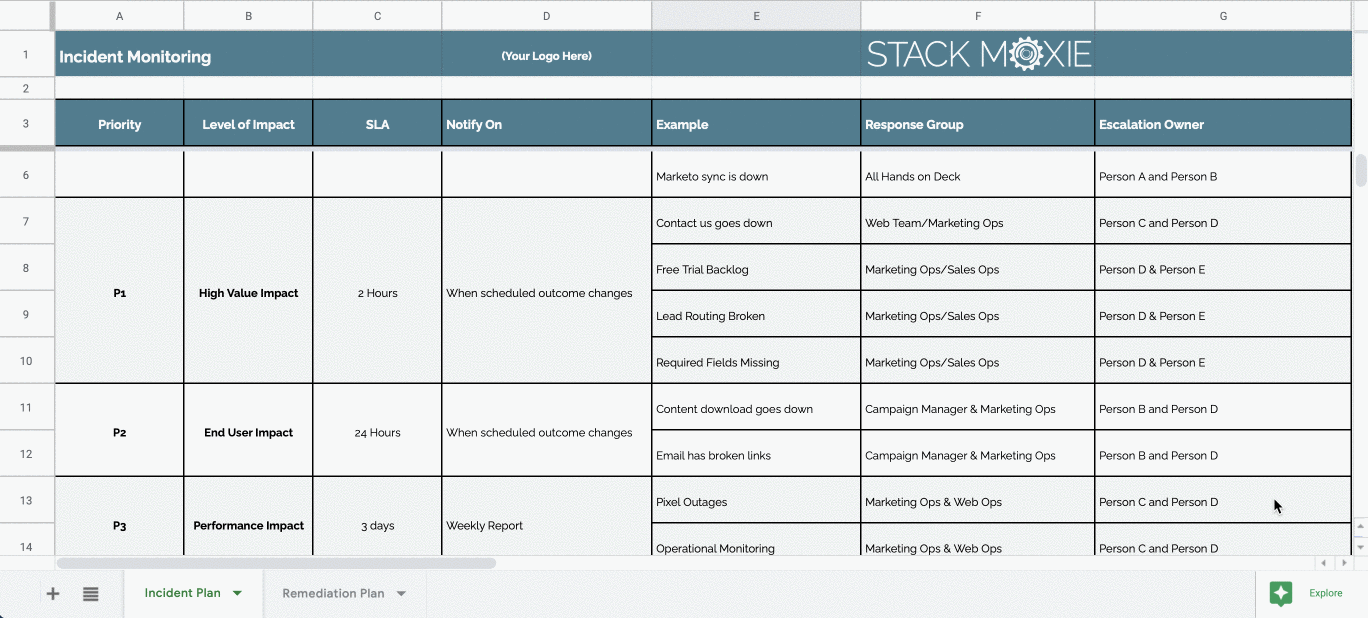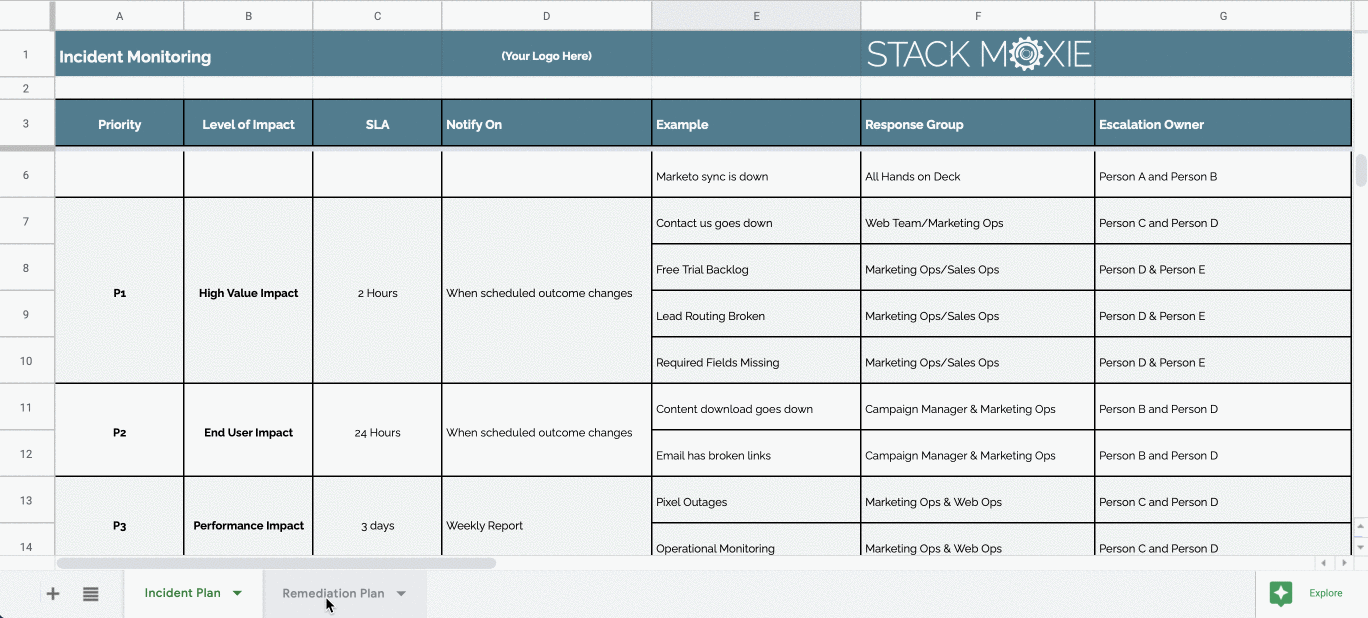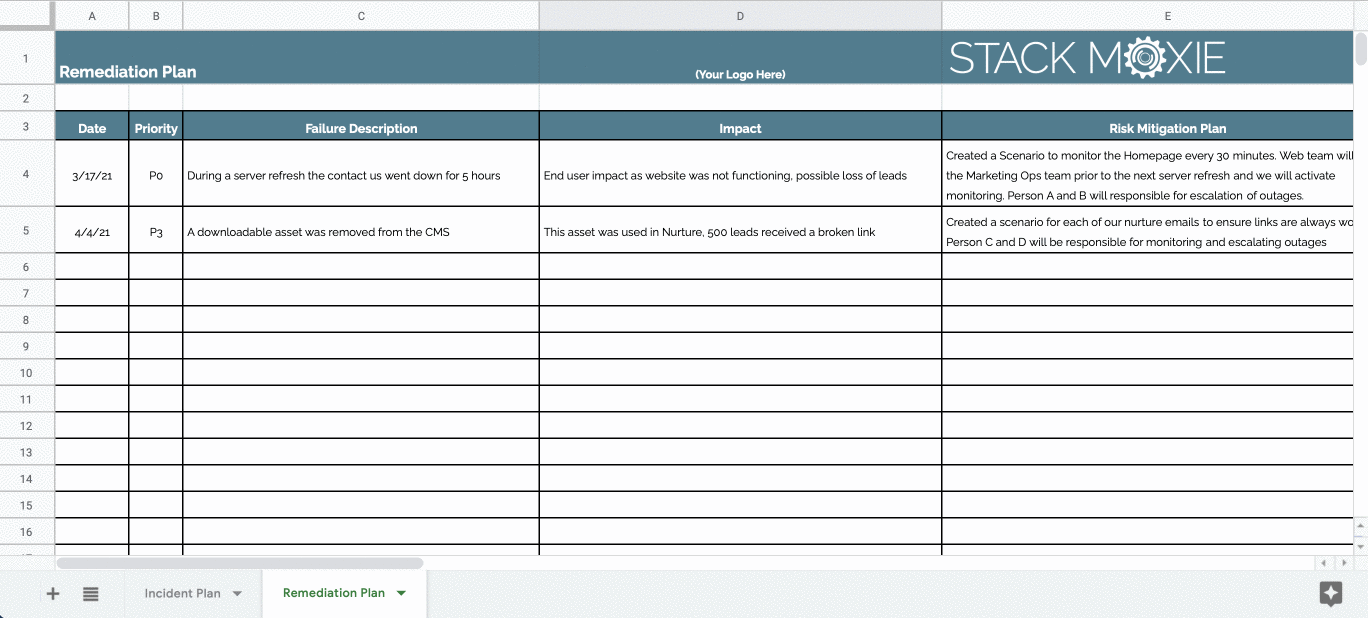
Incident & Remediation Plan Template for managing critical errors and
17 Task Worksheet Template /
Free Vulnerability Assessment Plan Template Google Docs, Word, Apple
30 Security assessment Plan Template Security assessment, Business
ICVulnerabilityRemediationPlanTemplate_Google.xltx Google Sheets
Vulnerability Management Program Template Stcharleschill Template
Vulnerability Remediation Plan Template Flyer Template
Free Vulnerability Assessment Templates Smartsheet
Eset Vulnerability & Patch Management.
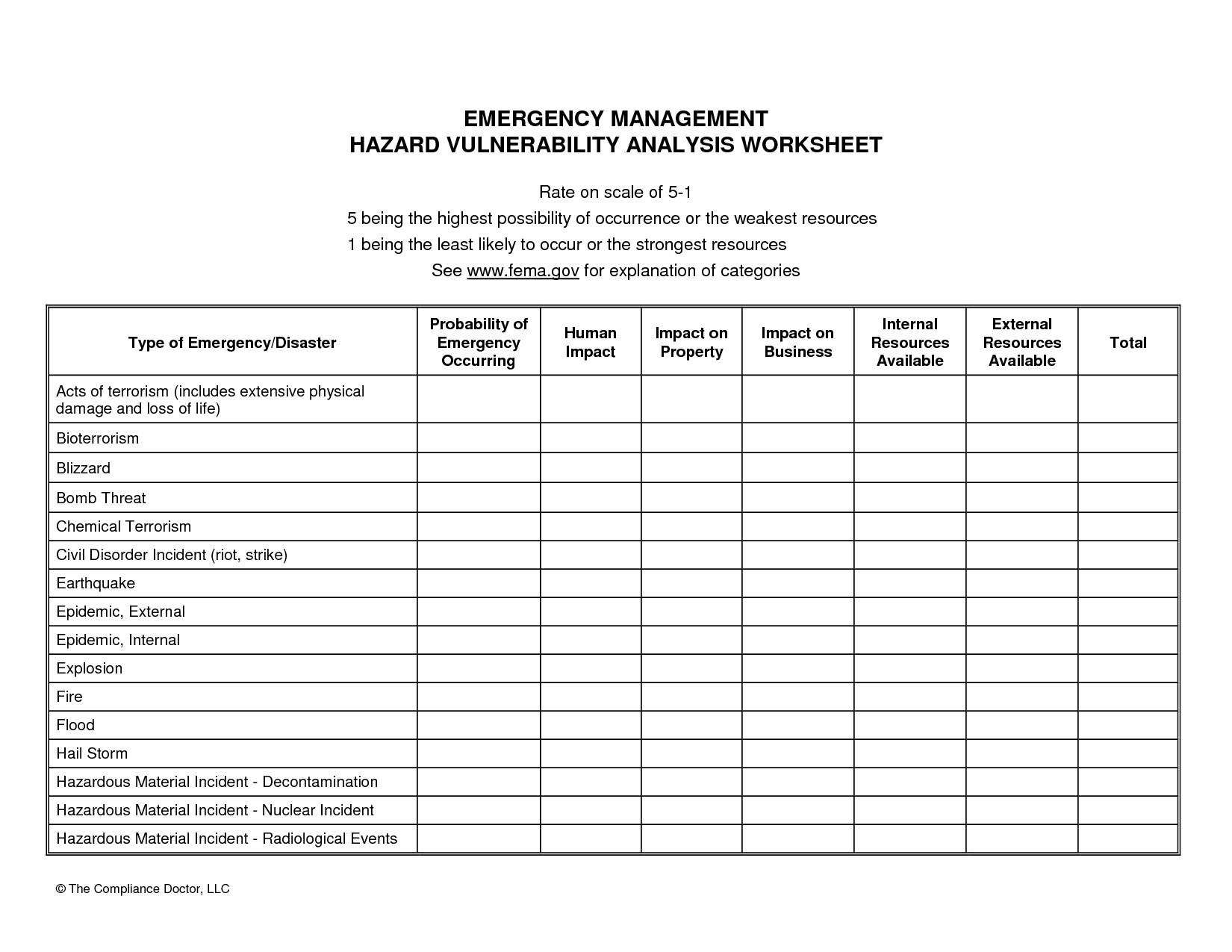
Web • High Vulnerabilities Should Be Remediated Within 30 Calendar Days Of Initial Detection.
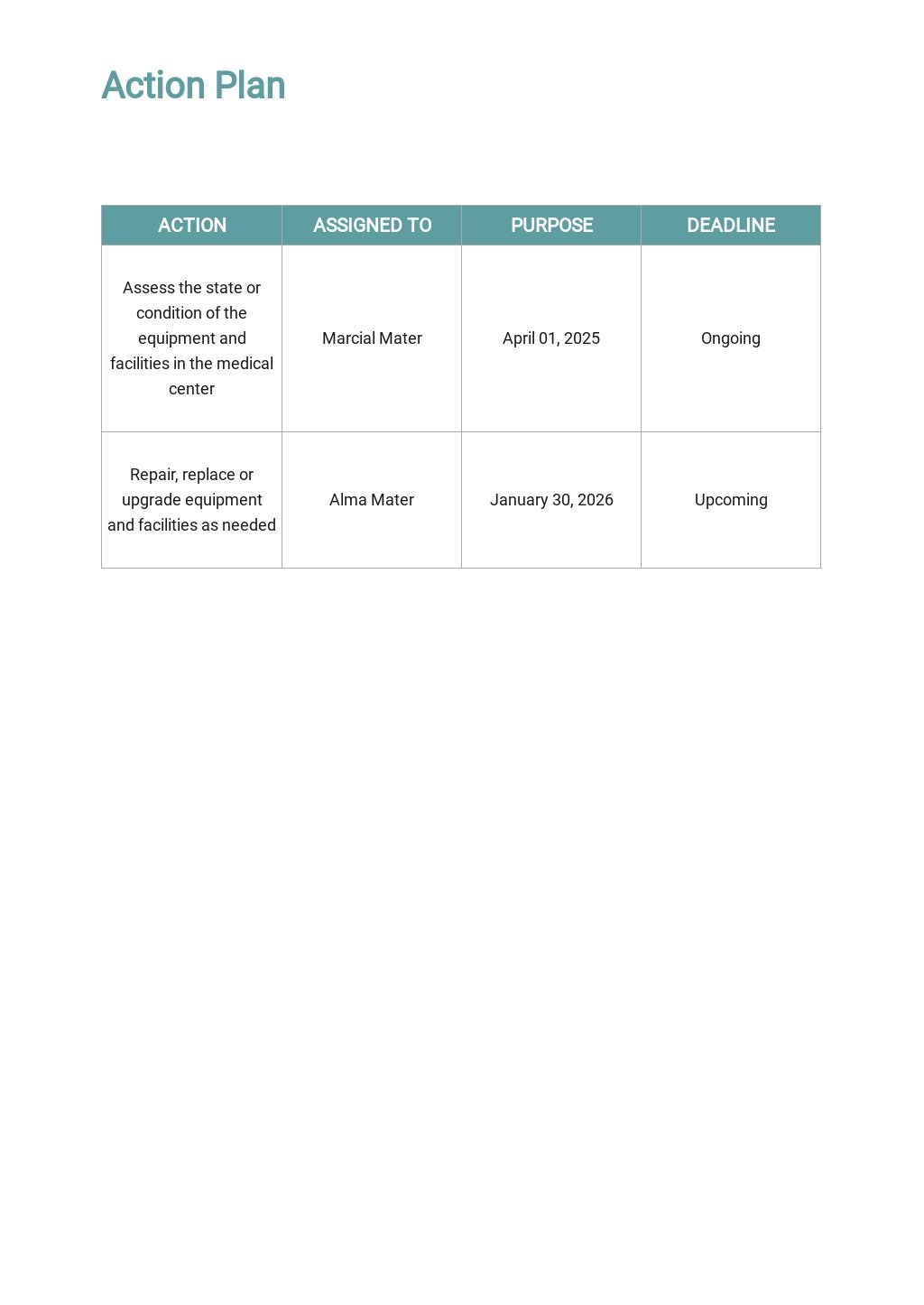
Risk Mitigation Planning Is The Process Of Developing Options And Actions To Enhance Opportunities And Reduce.
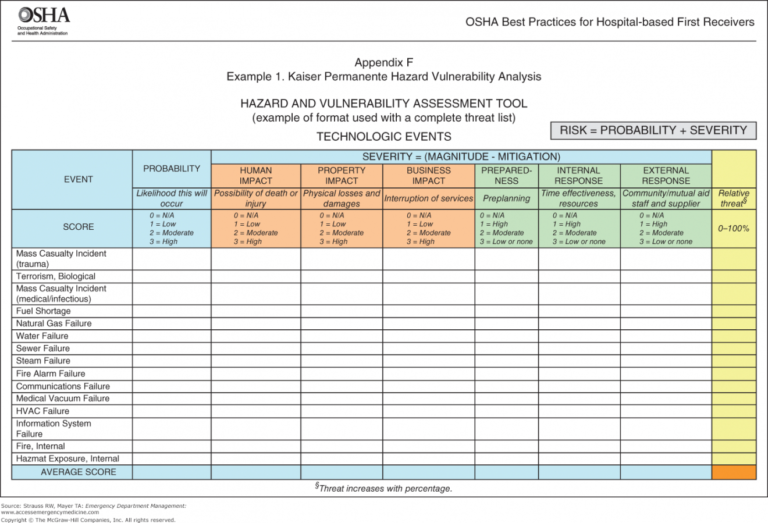
Web Vulnerability Remediation Plan Template Client Name Date Address Line 1 Address Line 2 Component Weakness Description Hardware Needed.
Related Post: