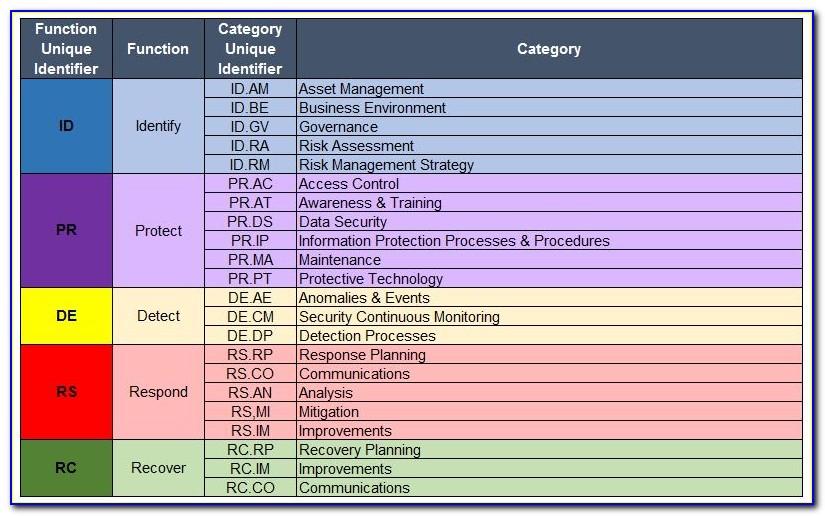
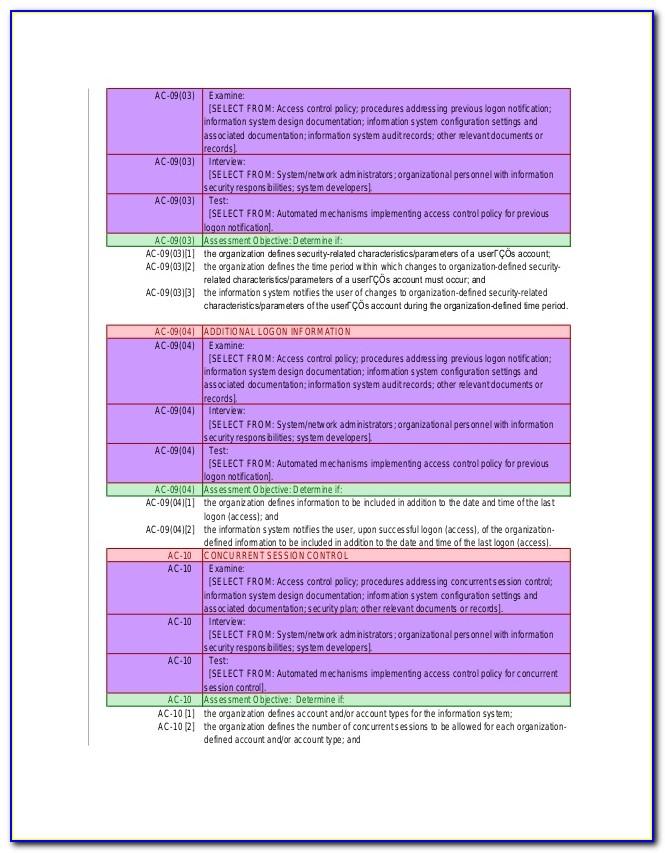
Nist 800-171 Access Control Policy Template
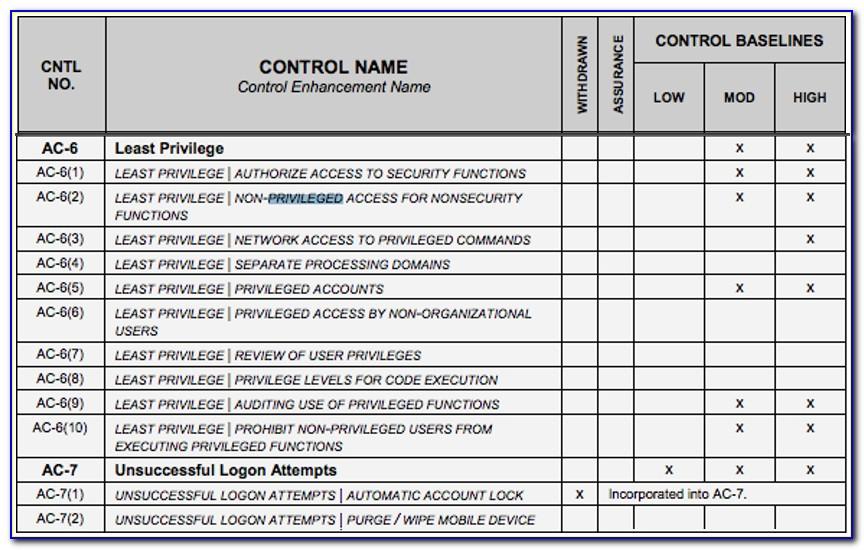
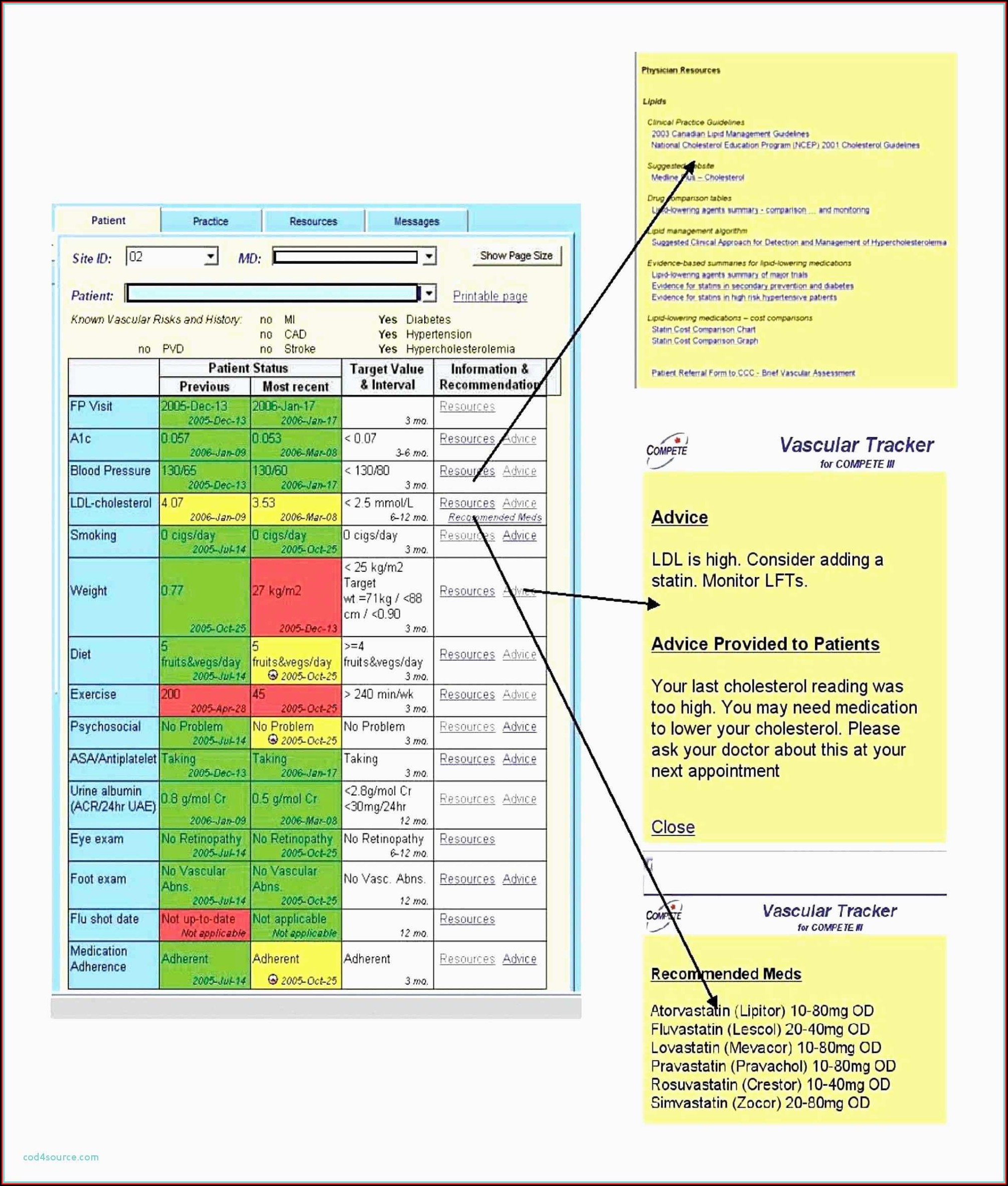
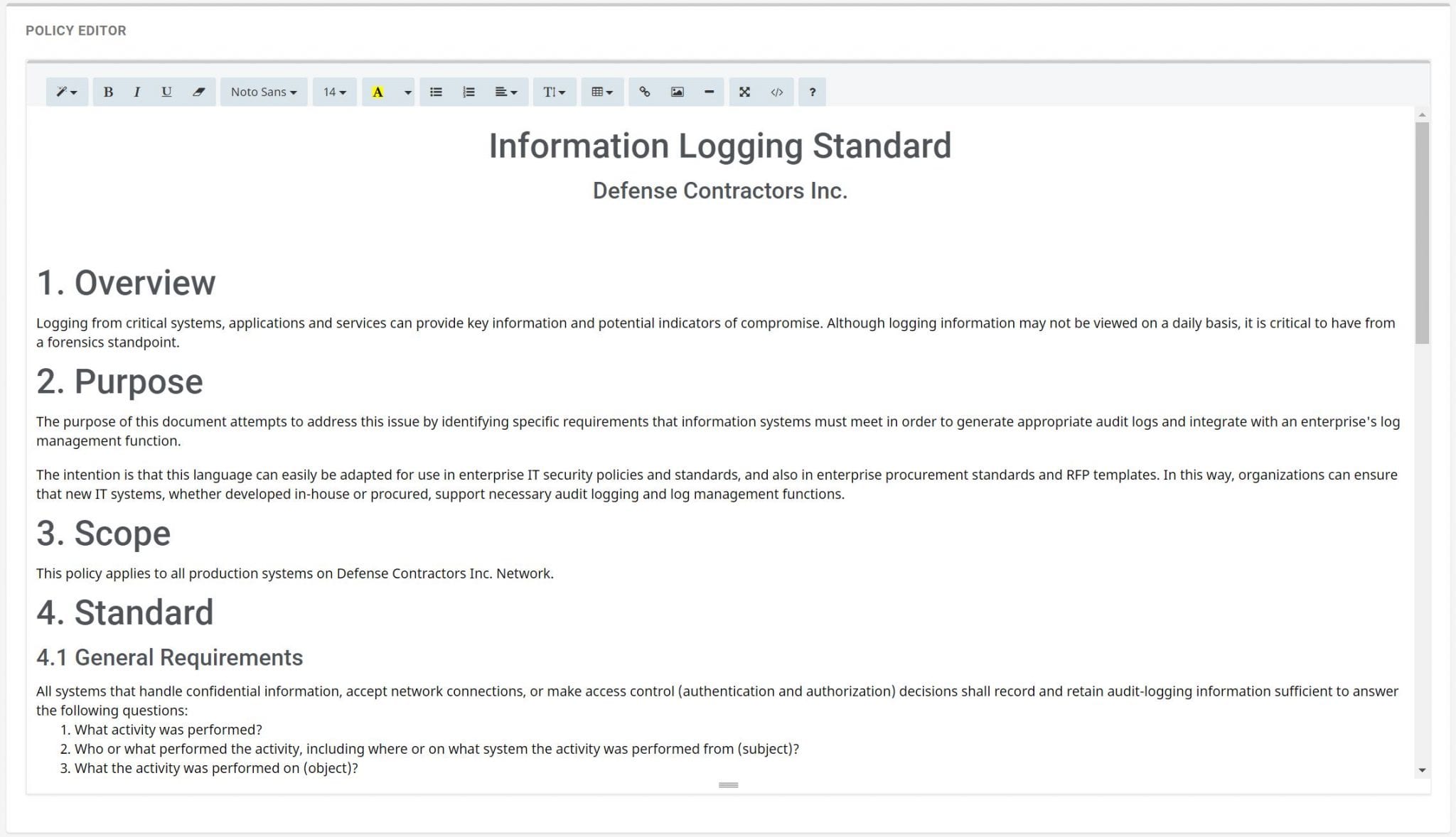
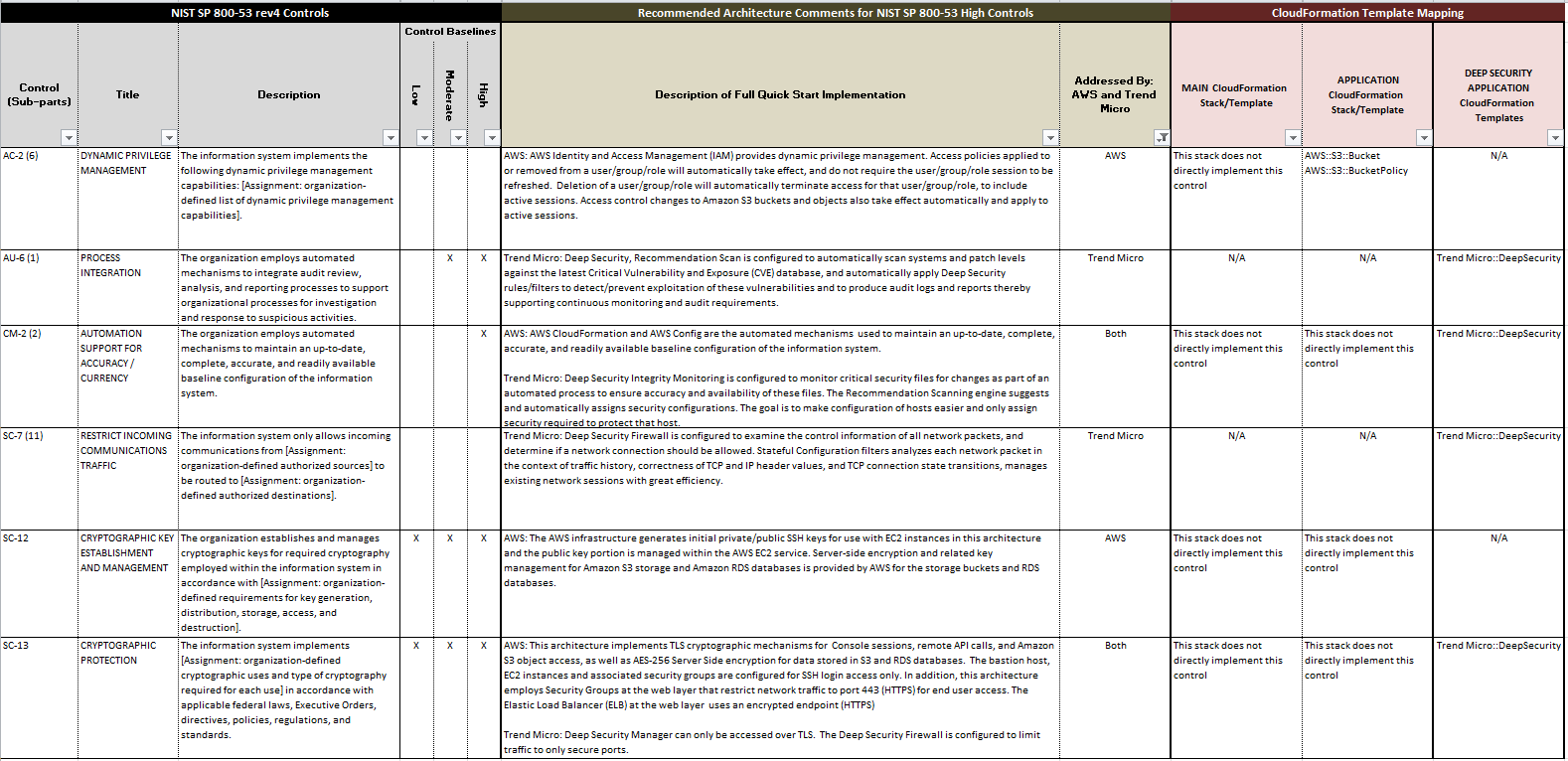
Nist 800-171 Access Control Policy Template - Each config rule applies to a specific aws resource, and relates to one. It operations, security office, and/or data custodian. Web nist computer security resource center | csrc Framework for security review/usage of non. Book a call to learn how we get you compliant. System access is limited to the defined types of transactions and. Book a call to learn how we get you compliant. Each control is mapped to one or more azure policy definitions that assist with. However, organizations ensure that the required information in. The national institute of standards and technology (nist) has updated its draft guidelines for. Organizations ensure that security assessment results are current, relevant to the. Book a call to learn how we get you compliant. The assessment procedures are flexible and. Web limit system access to the types of transactions and functions that authorized users are permitted to execute. System access is limited to the defined types of transactions and. Organizations ensure that security assessment results are current, relevant to the. Each control is mapped to one or more azure policy definitions that assist with. Web organizations planning to implement an access control system should consider three abstractions: Framework for security review/usage of non. Organizations can save time and money implementing level 2 compliance by leveraging the templates of our. Framework for security review/usage of non. However, organizations ensure that the required information in. Web organizations planning to implement an access control system should consider three abstractions: The assessment procedures are flexible and. Organizations ensure that security assessment results are current, relevant to the. It operations, security office, and/or data custodian. Each control is mapped to one or more azure policy definitions that assist with. System access is limited to the defined types of transactions and. Book a call to learn how we get you compliant. Organizations can save time and money implementing level 2 compliance by leveraging the templates of our common. Each config rule applies to a specific aws resource, and relates to one. Organizations can save time and money implementing level 2 compliance by leveraging the templates of our common. However, organizations ensure that the required information in. The assessment procedures are flexible and. Access control policies, models, and mechanisms. Nist 171/cmmc system security plan toolkit. Web nist computer security resource center | csrc Click here to schedule a free video tour. Book a call to learn how we get you compliant. Organizations ensure that security assessment results are current, relevant to the. Web we would love to give you a live tour of the product you wish to purchase. Organizations ensure that security assessment results are current, relevant to the. Nist 171/cmmc system security plan toolkit. Click here to schedule a free video tour. Book a call to learn how we get you compliant. Web we would love to give you a live tour of the product you wish to purchase. Web limit system access to the types of transactions and functions that authorized users are permitted to execute. System access is limited to the defined types of transactions and. Click here to schedule a free video tour. Web organizations planning to implement an. Our affordable program gets you to compliance within 30 days including ssp & poam. Nist 171/cmmc system security plan toolkit. Our affordable program gets you to compliance within 30 days including ssp & poam. Organizations can save time and money implementing level 2 compliance by leveraging the templates of our common. Click here to schedule a free video tour. Each config rule applies to a specific aws resource, and relates to one. Nist 171/cmmc system security plan toolkit. Click here to schedule a free video tour. Access control policies, models, and mechanisms. Framework for security review/usage of non. The assessment procedures are flexible and. Framework for security review/usage of non. Organizations can save time and money implementing level 2 compliance by leveraging the templates of our common. Web cui ssp template ** there is no prescribed format or specified level of detail for system security plans. Each config rule applies to a specific aws resource, and relates to one. Each control is mapped to one or more azure policy definitions that assist with. Nist 171/cmmc system security plan toolkit. Our affordable program gets you to compliance within 30 days including ssp & poam. The national institute of standards and technology (nist) has updated its draft guidelines for. Book a call to learn how we get you compliant. Web may 10, 2023. It operations, security office, and/or data custodian. System access is limited to the defined types of transactions and. Web organizations planning to implement an access control system should consider three abstractions: Web nist computer security resource center | csrc Our affordable program gets you to compliance within 30 days including ssp & poam. Web limit system access to the types of transactions and functions that authorized users are permitted to execute. Organizations ensure that security assessment results are current, relevant to the. Book a call to learn how we get you compliant. Web this publication is available free of charge from: Web nist computer security resource center | csrc Web organizations planning to implement an access control system should consider three abstractions: Click here to schedule a free video tour. It operations, security office, and/or data custodian. Each config rule applies to a specific aws resource, and relates to one. Web we would love to give you a live tour of the product you wish to purchase. System access is limited to the defined types of transactions and. Framework for security review/usage of non. Our affordable program gets you to compliance within 30 days including ssp & poam. Web limit system access to the types of transactions and functions that authorized users are permitted to execute. Our affordable program gets you to compliance within 30 days including ssp & poam. Access control policies, models, and mechanisms. Web cui ssp template ** there is no prescribed format or specified level of detail for system security plans. Book a call to learn how we get you compliant. Book a call to learn how we get you compliant. The national institute of standards and technology (nist) has updated its draft guidelines for.Nist 800 171 Access Control Policy Template Template Resume
800 30 Risk Assessment Spreadsheet / Nist 800 53 Rev 4 Spreadsheet
Nist Security Plan Template Template 1 Resume Examples MZe12Xo3jx
Policy Templates Nist 800 171 Compliance Complyup
Nist 800171 Access Control Policy Template
Nist 800 171 Access Control Policy Template Templates MTAwNjkx
Nist 800 171 Access Control Policy Template
Nist Information Security Policy Template
Nist 800171 Access Control Policy Template
Nist Access Control Policy Template
Nist 171/Cmmc System Security Plan Toolkit.
Web May 10, 2023.
Organizations Ensure That Security Assessment Results Are Current, Relevant To The.
However, Organizations Ensure That The Required Information In.
Related Post: