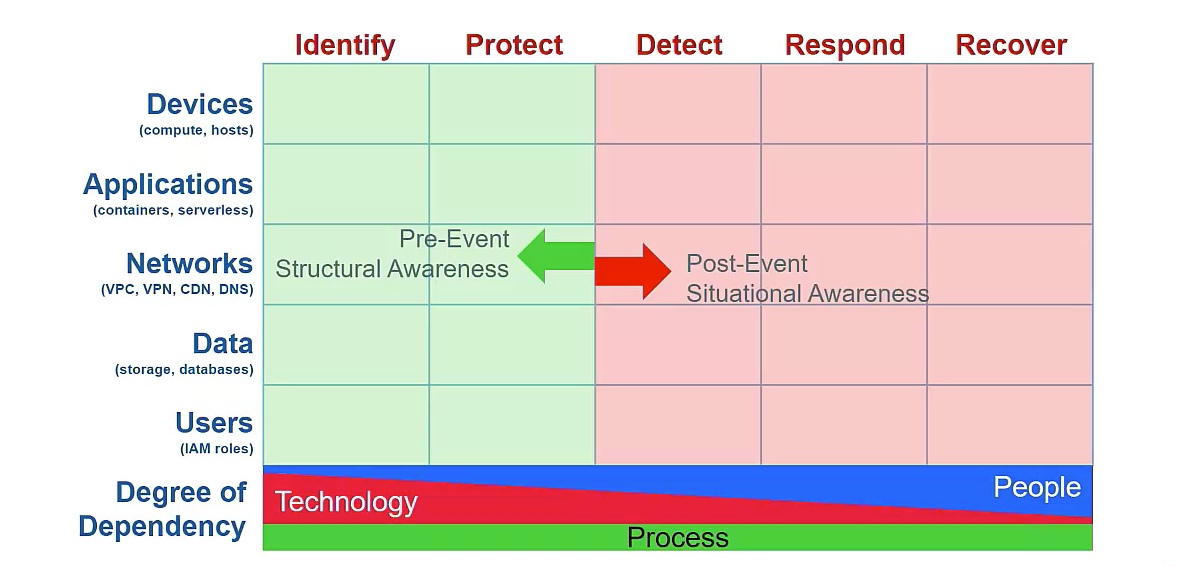
Cyber Defense Matrix Template
Cyber Defense Matrix Template - Web download cis controls v8 overview features resources cis controls at a glance the cis critical security controls (cis controls) are a prescriptive, prioritized, and simplified set. Cybersecurity practitioners can use this to organize. Inventorying assets and vulns, measuring attack surface, prioritizing, baselining normal,. This is an update to the cyber defense matrix briefing given at the 2019 rsa conference. Web request pdf | cyber defense matrix: This guide gives the correlation between 49 of. Web in applying each of the nist csf functions to them, the cyber defense matrix ensures that the full range of people, process, and technology capabilities can be. The dod cyber workforce framework establishes the dod’s authoritative lexicon based on the work an individual is performing, not their. Web join sounil and garrett gross of huntress to dive into how to understand and apply the cyber defense matrix. Web the ncsr question set represents the national institute of standards and technology cybersecurity framework (nist csf). This guide gives the correlation between 49 of. Web background on the cyber defense matrix. Web the matrix plots the five distinct functions of the nist cybersecurity framework (identify, protect, detect, respond, and recover) against the. A new model for optimal composition of cybersecurity controls to construct resilient risk mitigation | most enterprises aiming to. This is an update to. Web download cis controls v8 overview features resources cis controls at a glance the cis critical security controls (cis controls) are a prescriptive, prioritized, and simplified set. Identify, protect, detect, respond and recover. A new model for optimal composition of cybersecurity controls to construct resilient risk mitigation | most enterprises aiming to. Web join sounil and garrett gross of huntress. Web in applying each of the nist csf functions to them, the cyber defense matrix ensures that the full range of people, process, and technology capabilities can be. Web background on the cyber defense matrix. Web this document describes the methodology used to map the cis critical security controls (cis controls) to the cloud security alliance cloud control matrix. This. Web let’s first take a peek at an empty cyber defense matrix and then dig into the components that define its structure. During this webinar you will learn: Web dod cyber workforce framework. This is an update to the cyber defense matrix briefing given at the 2019 rsa conference. Web download categorization of cyber risks ppt. Web this document describes the methodology used to map the cis critical security controls (cis controls) to the cloud security alliance cloud control matrix. Identify, protect, detect, respond and recover. This is an update to the cyber defense matrix briefing given at the 2019 rsa conference. The dod cyber workforce framework establishes the dod’s authoritative lexicon based on the work. Web download categorization of cyber risks ppt. Cybersecurity practitioners can use this to organize. Web let’s first take a peek at an empty cyber defense matrix and then dig into the components that define its structure. A new model for optimal composition of cybersecurity controls to construct resilient risk mitigation | most enterprises aiming to. Identify, protect, detect, respond and. Web background on the cyber defense matrix. Web download categorization of cyber risks ppt. Web request pdf | cyber defense matrix: Web this report provides a survey of cyber threat modeling frameworks, presents a comparative assessment of the surveyed frameworks, and extends an existing framework to serve as. Web download cis controls v8 overview features resources cis controls at a. Web this report provides a survey of cyber threat modeling frameworks, presents a comparative assessment of the surveyed frameworks, and extends an existing framework to serve as. Web this document describes the methodology used to map the cis critical security controls (cis controls) to the cloud security alliance cloud control matrix. Web in applying each of the nist csf functions. Web download categorization of cyber risks ppt. Web in addition, the cyber defense matrix provides a mechanism to ensure that we have capabilities across the entire spectrum of options to help secure our environments. What threats face small and. Web the matrix plots the five distinct functions of the nist cybersecurity framework (identify, protect, detect, respond, and recover) against the.. Cybersecurity practitioners can use this to organize. What threats face small and. Web let’s first take a peek at an empty cyber defense matrix and then dig into the components that define its structure. Web this document describes the methodology used to map the cis critical security controls (cis controls) to the cloud security alliance cloud control matrix. Web request. Identify, protect, detect, respond and recover. Cybersecurity practitioners can use this to organize. Web let’s first take a peek at an empty cyber defense matrix and then dig into the components that define its structure. Web the ncsr question set represents the national institute of standards and technology cybersecurity framework (nist csf). Web join sounil and garrett gross of huntress to dive into how to understand and apply the cyber defense matrix. A new model for optimal composition of cybersecurity controls to construct resilient risk mitigation | most enterprises aiming to. Web download cis controls v8 overview features resources cis controls at a glance the cis critical security controls (cis controls) are a prescriptive, prioritized, and simplified set. This is an update to the cyber defense matrix briefing given at the 2019 rsa conference. Web background on the cyber defense matrix. What threats face small and. Web this document describes the methodology used to map the cis critical security controls (cis controls) to the cloud security alliance cloud control matrix. The dod cyber workforce framework establishes the dod’s authoritative lexicon based on the work an individual is performing, not their. Web dod cyber workforce framework. Web in addition, the cyber defense matrix provides a mechanism to ensure that we have capabilities across the entire spectrum of options to help secure our environments. Inventorying assets and vulns, measuring attack surface, prioritizing, baselining normal,. Web in applying each of the nist csf functions to them, the cyber defense matrix ensures that the full range of people, process, and technology capabilities can be. Web download categorization of cyber risks ppt. Web the matrix plots the five distinct functions of the nist cybersecurity framework (identify, protect, detect, respond, and recover) against the. Web this report provides a survey of cyber threat modeling frameworks, presents a comparative assessment of the surveyed frameworks, and extends an existing framework to serve as. This guide gives the correlation between 49 of. This guide gives the correlation between 49 of. Cybersecurity practitioners can use this to organize. This ppt template showcases the cybersecurity management action plan. This is an update to the cyber defense matrix briefing given at the 2019 rsa conference. Web this document describes the methodology used to map the cis critical security controls (cis controls) to the cloud security alliance cloud control matrix. Web the matrix plots the five distinct functions of the nist cybersecurity framework (identify, protect, detect, respond, and recover) against the. Web dod cyber workforce framework. Web download categorization of cyber risks ppt. Web in applying each of the nist csf functions to them, the cyber defense matrix ensures that the full range of people, process, and technology capabilities can be. A new model for optimal composition of cybersecurity controls to construct resilient risk mitigation | most enterprises aiming to. Web let’s first take a peek at an empty cyber defense matrix and then dig into the components that define its structure. Web request pdf | cyber defense matrix: Identify, protect, detect, respond and recover. What threats face small and. During this webinar you will learn: Web the ncsr question set represents the national institute of standards and technology cybersecurity framework (nist csf).Cyber Defense
What is the OWASP Cyber Defense Matrix?
Cyber Defense Matrix makes sense of chaotic security market Gadget Greed
The Cyber Defense Matrix eBook
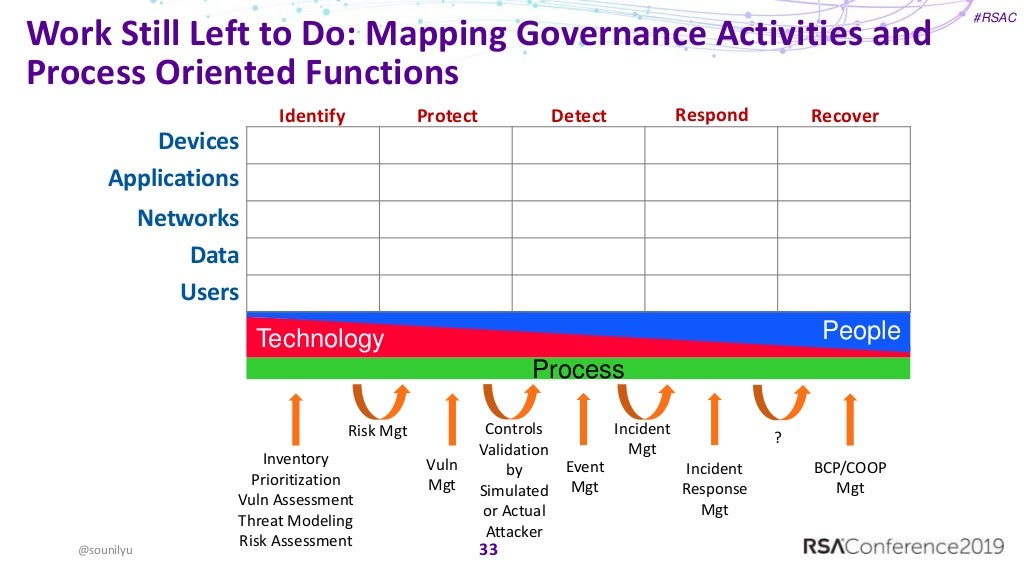
Map your cybersecurity gaps with the Cyber Defense Matrix
Cybersecurity Risk Assessment Template for creating cybersecurity
Mornington Peninsula Dandenong Cyber Security Update Extreme Networks
Cyber Defense Matrix Reloaded
【用Cyber Defense Matrix搭配資安框架改善資安弱點】資安策略成效要靠真實威脅調整 iThome
Prioritize Security Controls for Critical AWS Assets
Inventorying Assets And Vulns, Measuring Attack Surface, Prioritizing, Baselining Normal,.
Web This Report Provides A Survey Of Cyber Threat Modeling Frameworks, Presents A Comparative Assessment Of The Surveyed Frameworks, And Extends An Existing Framework To Serve As.
Web Download Cis Controls V8 Overview Features Resources Cis Controls At A Glance The Cis Critical Security Controls (Cis Controls) Are A Prescriptive, Prioritized, And Simplified Set.
The Dod Cyber Workforce Framework Establishes The Dod’s Authoritative Lexicon Based On The Work An Individual Is Performing, Not Their.
Related Post:

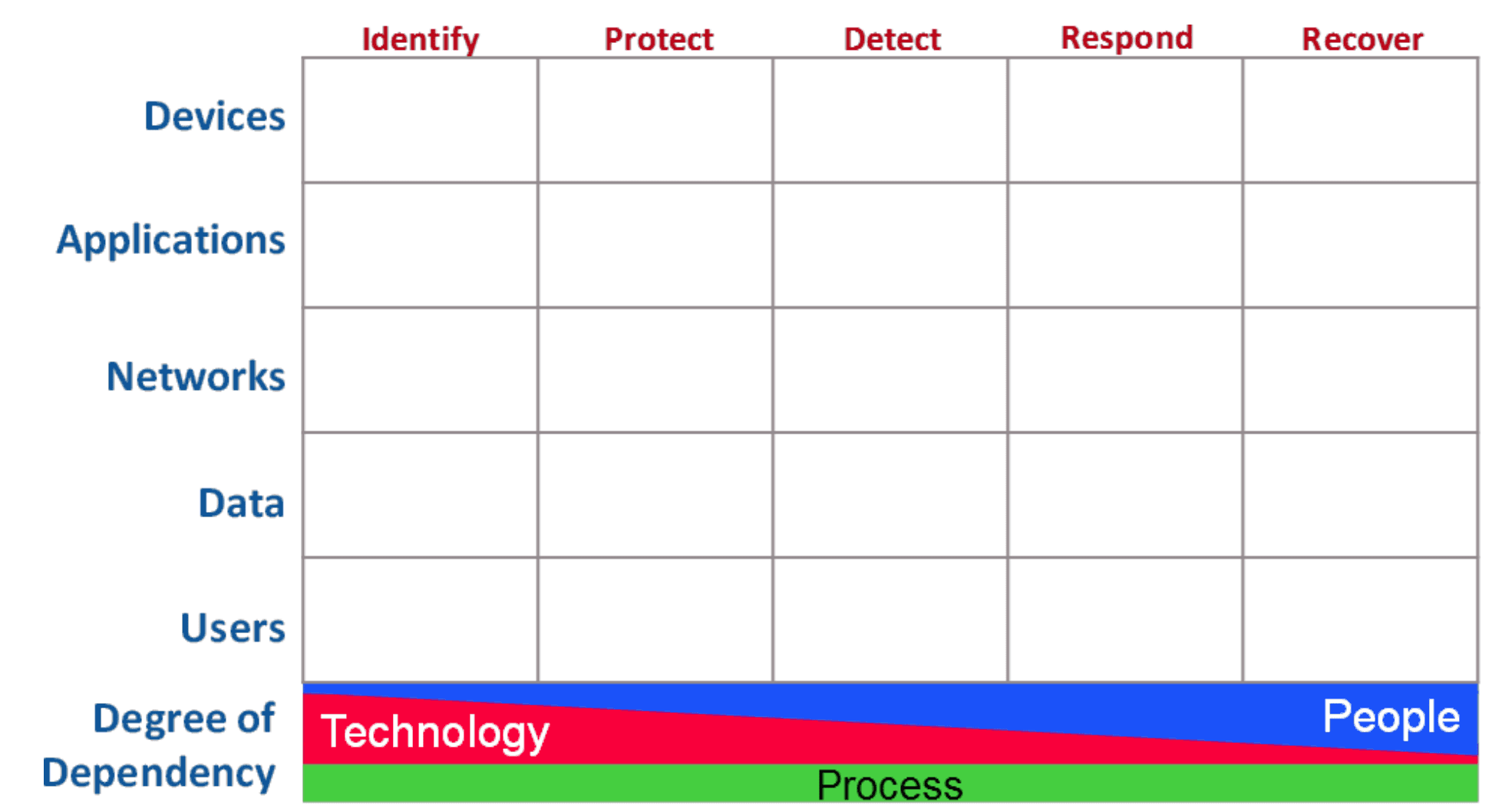
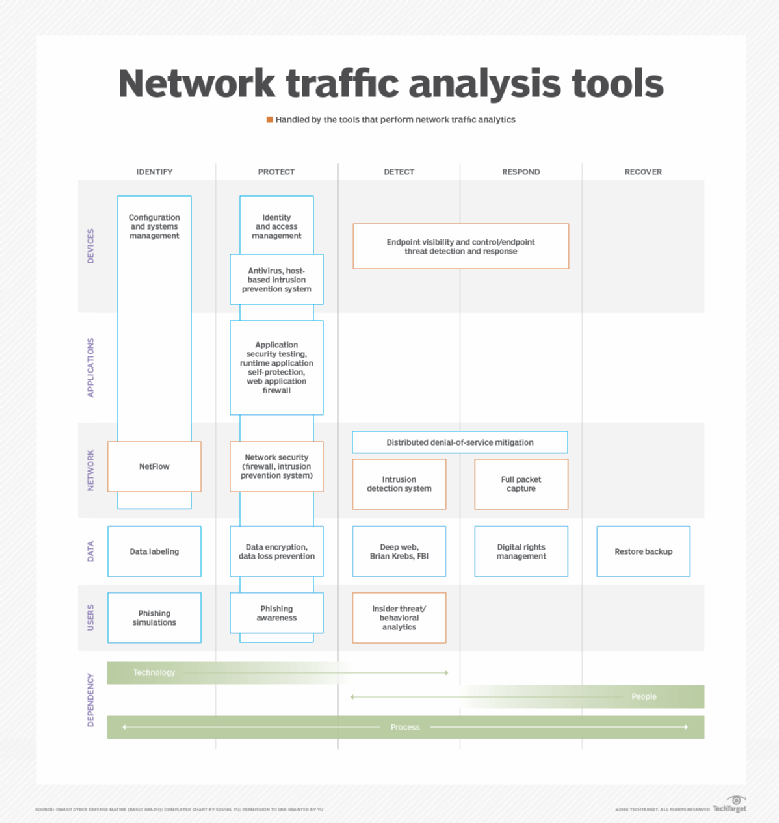



Part2_資安框架與Cyber Defense Matrix.jpg)