Access Management Policy Template
Access Management Policy Template - These are free to use and fully customizable to your company's it security practices. Access control policies, models, and mechanisms. Web sans has developed a set of information security policy templates. Protecting access to it systems and applications is critical to maintain the integrity of the northwestern polytechnic (“nwp”, or “the institution”). For more information about using aws cloudformation. A document designed for compliance with iso 27001:2022, iso 27001:2013, soc2 and pcidss. Train and educate users on access. Web free customizable privileged access management policy template. The templates can be customized and used as an outline of an organizational. Web organizations planning to implement an access control system should consider three abstractions: Web access control protects against unauthorized access to a computer system by using identification, authorization, authentication, and access approval techniques. Ad with delinea™, experience seamless and personalized privileged access management. A document designed for compliance with iso 27001:2022, iso 27001:2013, soc2 and pcidss. Easily find the policy management systems you're looking for w/ our comparison grid. These templates should be. Ad no matter your mission, get the right policy management systems to accomplish it. The templates can be customized and used as an outline of an organizational. Ad with delinea™, experience seamless and personalized privileged access management. One of the first steps to privileged access management success is defining clear and. Discover, manage, protect & audit privileged access for your. Easily find the policy management systems you're looking for w/ our comparison grid. Web use the workload view in clickup to monitor and review user access on an ongoing basis, ensuring compliance with your access policies. A document designed for compliance with iso 27001:2022, iso 27001:2013, soc2 and pcidss. Train and educate users on access. Web organizations planning to implement. Train and educate users on access. These templates should be used during the onboarding. A document designed for compliance with iso 27001:2022, iso 27001:2013, soc2 and pcidss. Protecting access to it systems and applications is critical to maintain the integrity of the northwestern polytechnic (“nwp”, or “the institution”). Web this tool contains four sample policies that define procedures for ensuring. Train and educate users on access. Edit the document's elements with our online. Ad with delinea™, experience seamless and personalized privileged access management. Web the policy templates are provided courtesy of the state of new york and the state of california. Discover, manage, protect & audit privileged access for your company at lightning speed Any user who requests access to. These templates should be used during the onboarding. Web access management authentication authorization federation bring your own identity credential, access management policy reason for the policy appropriate security. One of the first steps to privileged access management success is defining clear and. Access control policies, models, and mechanisms. The templates can be customized and used as an outline of an organizational. Ad with delinea™, experience seamless and personalized privileged access management. Web organizations planning to implement an access control system should consider three abstractions: • authentication credentials will not be coded into programs or queries. Web access control protects against unauthorized access to a computer system by using. The templates can be customized and used as an outline of an organizational. Web the policy templates are provided courtesy of the state of new york and the state of california. 24 oct, 2019, 08:01 et. Web access management authentication authorization federation bring your own identity credential, access management policy reason for the policy appropriate security. Web use the workload. 24 oct, 2019, 08:01 et. Discover, manage, protect & audit privileged access for your company at lightning speed Access control policies, models, and mechanisms. The templates can be customized and used as an outline of an organizational. Protecting access to it systems and applications is critical to maintain the integrity of the northwestern polytechnic (“nwp”, or “the institution”). One of the first steps to privileged access management success is defining clear and. Web free customizable privileged access management policy template. Web fully customizable privileged access management policy template increase understanding and oversight of privileged access management with a pam policy. Web you can use this sample policy as a starting point to build a pam policy for your. Web access control protects against unauthorized access to a computer system by using identification, authorization, authentication, and access approval techniques. A document designed for compliance with iso 27001:2022, iso 27001:2013, soc2 and pcidss. Train and educate users on access. Web the policy templates are provided courtesy of the state of new york and the state of california. Access control policies, models, and mechanisms. Web usage guidelines for each of the access templates is outlined on the team member enablement's handbook page. 24 oct, 2019, 08:01 et. Any user who requests access to. Web access management is the process of identifying, tracking, controlling, and managing user access rights to information systems. For more information about using aws cloudformation. Ad no matter your mission, get the right policy management systems to accomplish it. Web access management authentication authorization federation bring your own identity credential, access management policy reason for the policy appropriate security. These are free to use and fully customizable to your company's it security practices. • authentication credentials will not be coded into programs or queries. Web use the workload view in clickup to monitor and review user access on an ongoing basis, ensuring compliance with your access policies. Edit the document's elements with our online. Web this tool contains four sample policies that define procedures for ensuring that access to all systems and applications is properly approved and monitored. Web fully customizable privileged access management policy template increase understanding and oversight of privileged access management with a pam policy. Discover, manage, protect & audit privileged access for your company at lightning speed Web all systems and applications must use encrypted authentication mechanisms and abide by the following: Web organizations planning to implement an access control system should consider three abstractions: Web access management is the process of identifying, tracking, controlling, and managing user access rights to information systems. Web access control protects against unauthorized access to a computer system by using identification, authorization, authentication, and access approval techniques. These are free to use and fully customizable to your company's it security practices. Web you can use this sample policy as a starting point to build a pam policy for your organization. Protecting access to it systems and applications is critical to maintain the integrity of the northwestern polytechnic (“nwp”, or “the institution”). Web sans has developed a set of information security policy templates. Web this tool contains four sample policies that define procedures for ensuring that access to all systems and applications is properly approved and monitored. These templates should be used during the onboarding. Web access management authentication authorization federation bring your own identity credential, access management policy reason for the policy appropriate security. One of the first steps to privileged access management success is defining clear and. A document designed for compliance with iso 27001:2022, iso 27001:2013, soc2 and pcidss. Discover, manage, protect & audit privileged access for your company at lightning speed 24 oct, 2019, 08:01 et. Ad with delinea™, experience seamless and personalized privileged access management. Discover, manage, protect & audit privileged access for your company at lightning speedSample IT Security Policy Template 9+ Free Documents Download in Word
Remote Access Policy Word Template PDF Wi Fi Wireless Access Point
Standard Access Control Policy Template Free Download
Standard Access Control Policy Template Free Download
Nist Access Control Policy Template
1.07 Secure Data Center Access Policy Exports Government Information
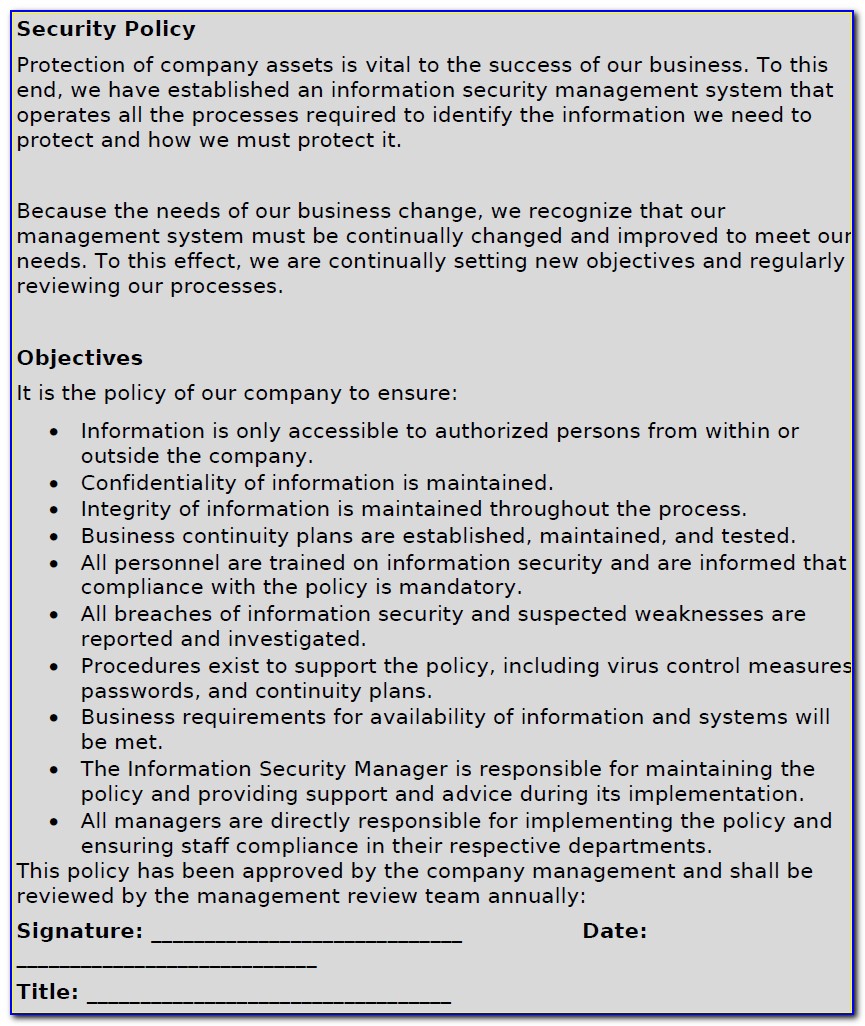
Iso 27001 Isms Policy Template
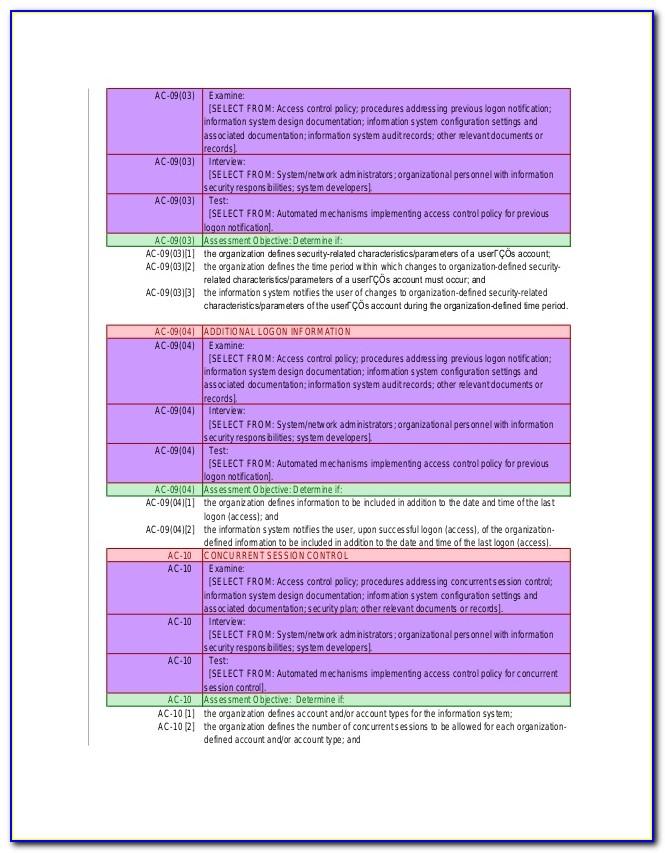
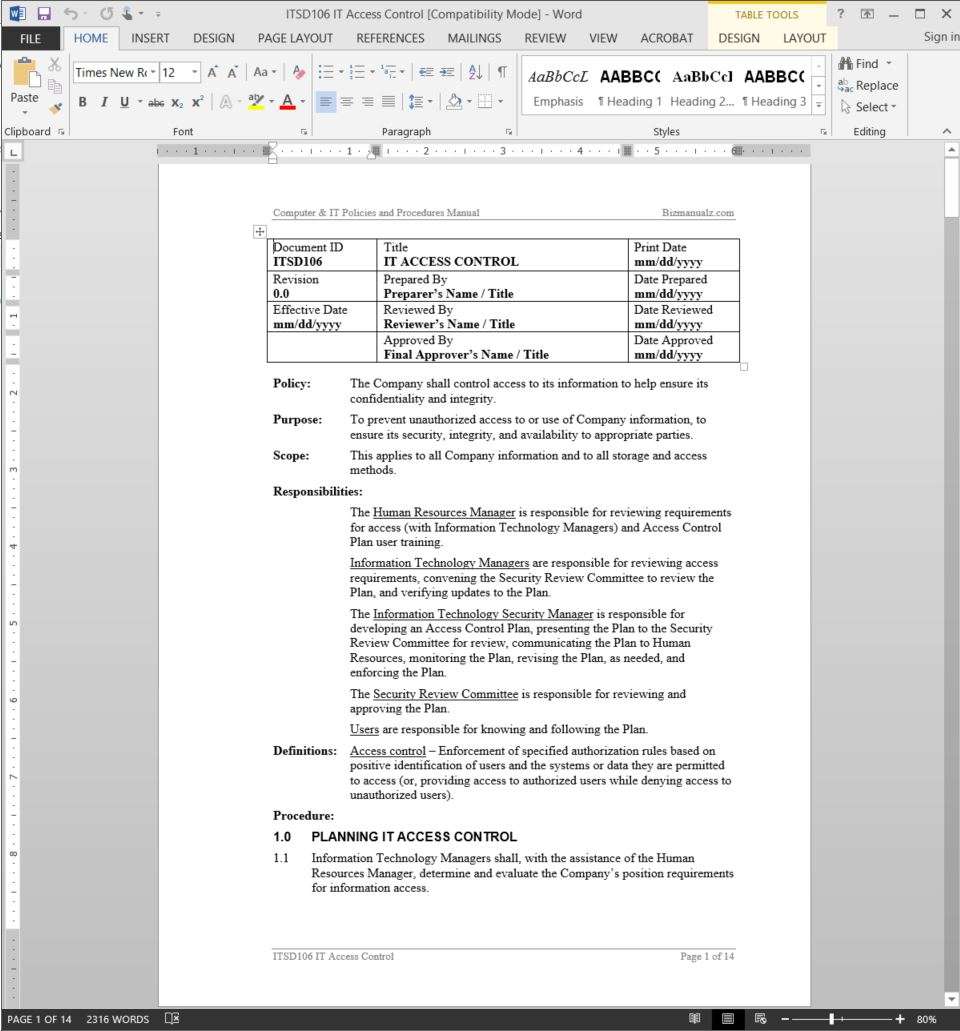
IT Access Control Policy Access Control Policies And Procedures
Standard Access Control Policy Template Free Download
Standard Access Control Policy Template Free Download
Access Control Policies, Models, And Mechanisms.
Web Use The Workload View In Clickup To Monitor And Review User Access On An Ongoing Basis, Ensuring Compliance With Your Access Policies.
Web The Policy Templates Are Provided Courtesy Of The State Of New York And The State Of California.
Web Usage Guidelines For Each Of The Access Templates Is Outlined On The Team Member Enablement's Handbook Page.
Related Post: